The SnackHack2 source code can be found on my GitHub with the link. More information about this tool, can be found at my other article with the name SnackHack2: Hacking tool and Recon.
Port Scanning IPs
This script will perform a port scan of the first 1,000 ports. The code will create a new file, with a name like “127.0.0.1_port_scan”. Since “delete” is set to true, after extracting all the scans with port “22” open. The code will delete the files and save all the IPs with port 22 open in one file.
require './lib/snackHack2'
for i in 0..255
puts "167.71.98.#{i}"
tcp = Snackhack2::PortScan.new
tcp.ip = "167.71.98.#{i}"
tcp.run
i += 1
print("\n\n")
end
tcp.delete = true
tcp.ports_extractor("22")
Getting Information About a Site
The ruby gem “colorize” must be installed for this script. Snackhack2 also needs to be installed. The code will perform a bunch of different tests on the site to figure out what CMS the site is using, the webserver version, it will check to see if the site is using Google Analytics, as well as perform banner grabbing and checking the site’s Robots.txt file for open or sensitive directories. The code will also list the site’s meta data tag.
require 'snackhack2'
require 'colorize'
print("Enter URL (with HTTPS://): ")
url = gets.chomp
print("\n\n\n")
puts "[+] Checking for Drupal...\n".red
Snackhack2::Drupal.new(url).all
puts "--------\n"
puts "[+] Checking for WordPress...\n".red
Snackhack2::WordPress.new(url).run
puts "--------\n"
puts "[+] Checking for TomCat...\n".red
Snackhack2::TomCat.new(url)
puts "--------\n"
puts "[+] Checking the site for Google Analytics...\n".red
Snackhack2::GoogleAnalytics.new(url).run
puts "--------\n"
puts "[+] Grabbing the Banner...\n".red
Snackhack2::BannerGrabber.new(url).run
puts "--------\n"
puts "[+] Checking Robots.txt...\n".red
Snackhack2::Robots.new(url).run
puts "--------\n"
puts "[+] Checking Website Meta...\n".red
Snackhack2::WebsiteMeta.new('https://x.com').run
puts "--------\n"Remote SSH Forwarding
More information about SSH Forwarding can be found here. There are a couple other types of SSH such as forward SSH and local SSH. I would definitely check out the site listed above. There are some pretty cool stuff that can be done with SSH tunneling. Like for example you could run a local website on one server or VPS and then create a SSH tunnel where you can tunnel your traffic so that you can access the locally hosted server. You could use a SSH tunnel for a box to connect back to your machine, creating a reverse shell that you can remotely connect and run commands on a remote box.
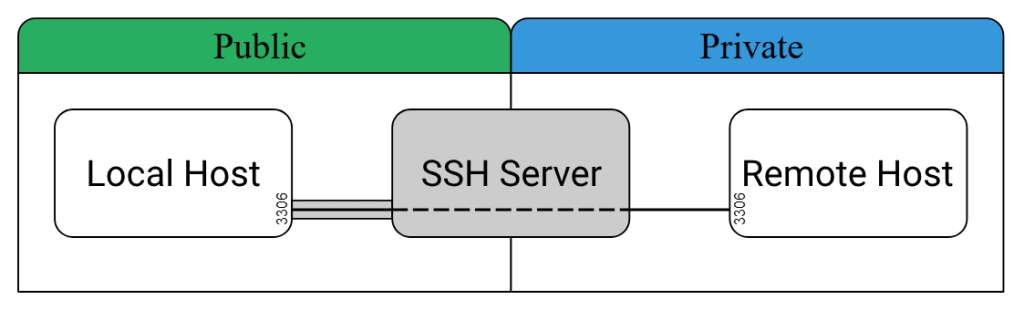
require './lib/snackHack2'
ssh = Snackhack2::SSHForwardRemote.new
ssh.site = "187.171.198.132"
ssh.user = "root"
ssh.pass = "secretpassword"
ssh.key = "/home/JakeFromStateFarm/.ssh/id_rsa"
ssh.lport = 2222
ssh.lsite = "localhost"
ssh.rport = 8022
ssh.runBanner Grabbing Multiple Sites
This scripts takes the URLS that are contained in an array and loops through all the elements of the array. The script calls the “Snackhack2::BannerGrabber” class and gets the banner of the site using cURL which it prints the results in the terminal. Banner grabbing can be used to try to guess what server is running a website. Which could allow an attacker to see if the web server version is vulnerable to a exploit.
bg = ["https://google.com",
"https://kinsta.com", "https://porchlightshop.com", "https://www.drrajatgupta.com"]
bg.each do |site|
Snackhack2::BannerGrabber.new(site).curl
end Checking Sites for WordPress
This script will check for WordPress users, perform a port scan on the site and grab the site’s meta data. For this gem to work, the colorize gem needs to be installed. This gem can be installed by running the command: gem install colorize. Meta elements are tags used in HTML to document meta data about the site like social media URLS, keywords, authors and the description of the site.
require './lib/snackHack2'
require 'colorize'
print("Enter URL ( with https:// ):")
url = gets.chomp
puts "WordPress\n\n".blue
wp = Snackhack2::WordPress.new(url)
wp.users
puts "\n\n"
puts "Port Scan the Site\n\n".green
ps = Snackhack2::PortScan.new
ps.ip = url.gsub("https://", "")
ps.run
puts "\n\n"
puts "WebSite META DATA\n\n".red
Snackhack2::WebsiteMeta.new(url).run
puts "\n\n"
puts "Get ALL Links...\n\n\n".yellow
Snackhack2::WebsiteLinks.new(url).run
