Happy Cybersecurity Awareness Month, this article is about metadata and how it might affect you. Please check out my last post which is titled, “Spotting Phishing Emails“
Table of Contents
According to Wikipedia metadata is “data that provides information about other data, but not the content of the data itself, such as the text of a message or the image itself.“
Operations security, also known as Op sec, is the process of limiting the amount of information about yourself on the internet. The old verbiage and loose lips sink ships still hold water. The Internet is forever, think to yourself do you want this information to be on the Internet forever? Be sure to remove any metadata before posting images on the internet. Some sites will automatically strip the data. But if you are worried you should remove the metadata yourself in case the site does not strip the metadata.
Meta Data in Documents

In the digital age, you have to be careful what you post, and what you share. Back to metadata, did you share Word documents that can expose some of your personal information such as your email, the time and date the file was modified, and even how long you worked on the document? For example, the image below shows the metadata from a document.
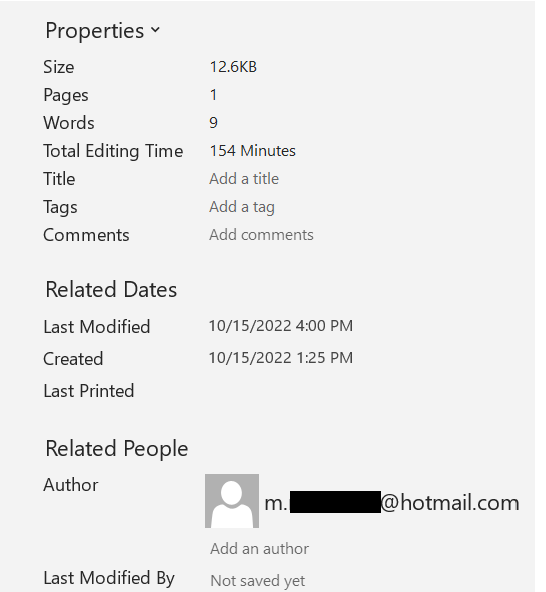
The example shows the author’s email. The author edited the file for 154 minutes, the date and time the file was last modified, and the date and time that the file was created. A teacher or professor could use the metadata in an assignment to see how long it took the student to write an assignment. A teacher could also use the metadata of the documents to see when the student started the assignment.
A threat actor could download a file from your company’s site and obtain the email of the administrator’s assistant which could be used to send a phishing email to them. A threat actor could also use the email to search hacked databases for the user’s password they used in the past.
I was watching a documentary about the serial killer known as BTK. He murdered ten people between 1974 to 1991. In 2004 he started to send the police and media more letters. In one letter he wrote to the police asking if a floppy disk could be traced. If the police could not trace the floppy disks the police were to put an ad in the newspaper.
Of course, the police lied to him, saying that it could not be traced. Anyways BTK sent the police a floppy disk with a letter. Investigators found the document that BTK attended them to see but investigators also found a couple of deleted files, one with files containing the words, “Christ Lutheran Church”. The deleted file’s metadata showed that the user who last modified the file had the username of “Dennis”. Equipped with that information, investigators quickly discovered that the BTK was Dennis Raider.
Meta Data in Images
Did you know that if you take a picture with your phone the Geo coordinates could be imbedded in a picture? Well, it is true! Phones and even non-phone cameras can show the GPS location of where the picture was taken. In 2012, VICE wrote about John McAfee who at the time was on the run of from the police. In the article, Vice included a photograph of John, but they forgot to wipe the metadata in the file.
Researchers soon discovered the exact Geo coordinates of where John was staying at the time. Luckily on most modern phones, you can disable the feature that will include your geo coordinates in the image. There are even tools online that can be used to view metadata in images and remove it. Most sites like Facebook, and Twitter ( X ) remove metadata before posting due to security concerns.

The image above shows how an images can have the location embedded into the file. Also shows the time that the image was taken, which was October 21st at 9:01 PM.
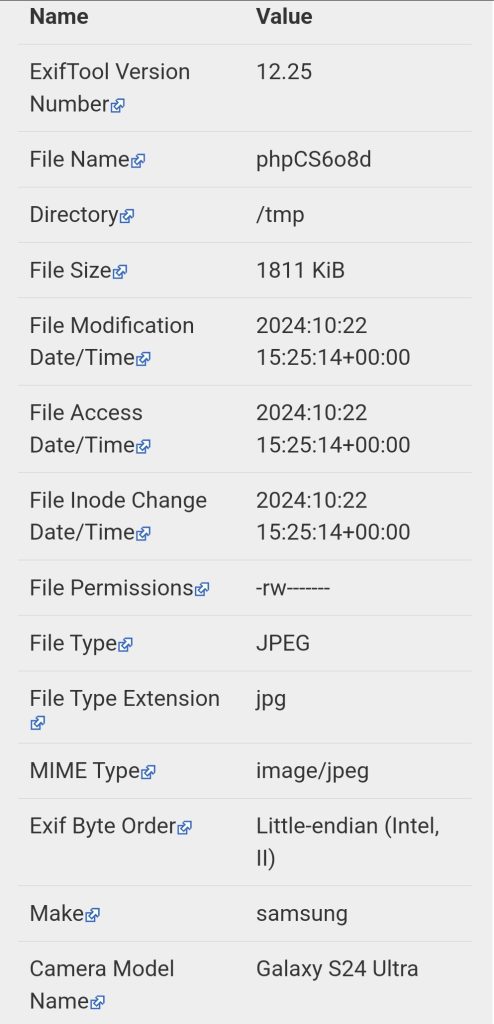
In the image above I used a site to extract Exif or metadata from the image. Doing the show gave us information on what type of device the image was taken on. In this example, the camera Model name shows that the camera used was my Galaxy S24 Ultra. The metadata also shows the make of the device used to take the image made was Samsung. This information might seem harmless but it gives an attacker information about the type of devices you use.
Once they know the operating system of your phone, they could target you with Android malware.
If you are on vacation, wait until you get back from vacation to post on social media. Thieves could target your house if they know you will be out of town. It is easy to get the name of a house owner due to the fact that the information is public.
How Stores Are Tracking you via Metadata while Shopping
Stores are starting to use Bluetooth technology in stores to track your movements while shopping. Every phone has a different Bluetooth beacon that stores can use to track your movement while shopping. They might be used to measure areas of high foot traffic, detect shoplifting, or even used to track regular customers’ movement as they shop for their goods. Using the information they might show you advisements based on areas where you spent the most time. Some big chain stores have monitors hidden in the ceiling or racks that are used to track your movement throughout the store.
Rewards systems are nice, you can get some nice deals but did you know that stores can use that reward data to put a name to the items you buy? One way of protecting yourself is to turn off your Bluetooth when shopping. Another is to use cash when buying sensitive items. The only problem is that you would not be able to listen to music while shopping.
Especially since newer phones do not have aux plugs anymore. Stores will often try to get you to download the store’s app, this is another way that the store can track you and your movements while shopping. Before shopping you should turn off permissions like WIFI or Bluetooth on the store’s app. Maybe even leave your phone in your car.
Turning off Wi-Fi when shopping as your phone will broadcast your past connected networks. This could also be used to track your movements while at the store. Do not join the store’s Wi-Fi either, this could be used to track your movements while shopping, locate where you live, and build a profile of your shopping habits.
Rewards programs are nice as they can be used for free items or be a way to find deals, but they could also be used by a store to tie your name to the products you buy. Which could be used to categorize your shopping habits. Like if you buy painkillers every month, this information could be sold to data brokers or used to send personalized advertisements. For example, they could determine if you are a smoker, drinker of alcohol, or any other type of habit. When shopping try to turn off your Wi-Fi, and Bluetooth and limit the use of rewards apps.
Years ago, the store Target was able to detect that a woman was pregnant based on items she bought. Target realized that pregnant women bought certain products. Based on those products Target gave shoppers a score which if a threshold was met, they would send the person advertisements or deals. This woman met the threshold and Target promptly sent her advertisements and deals for products that pregnant women could use. The store, Target might of used its award program to tie names to purchases. Rewards programs are awesome, they usually have great deals or coupons, but is it worth your privacy? I cannot answer the question for you but I think privacy is really important and something you should try to protect at all costs. Even if you think you have nothing to hide. It is the principle if you do not protect and fight for your privacy it could be taken away.
