Check out my other article titled “Staying Safe on Social Media“. This is apart of a series for Cybersecurity month.
Table of Contents

In this article, I will show the principles used by threat actors in phishing emails with the goal of teaching the reader how to spot phishing emails.
In the modern world, phishing emails will often not have bad grammar or spelling mistakes. Especially in the age of Artificial intelligence. Threat actors are increasingly utilizing AI to create phishing emails. The whole goal of sending phishing emails is to try to get the person to enter their personal information, click a link, or download a file. The threat actor or hacker will use the following principles to try to get you to enter your information, click a link, or download a file. A lot of time a phisher will use multiple of the principles listed below in the same email to maximize the impact on the user.
- Authority
- Imitation
- Scarcity
- Familiarity
- Trust
- Urgency
- Consensus
In this article I will go over all seven of the principles in details. I will also be showing examples of phishing emails.
Authority
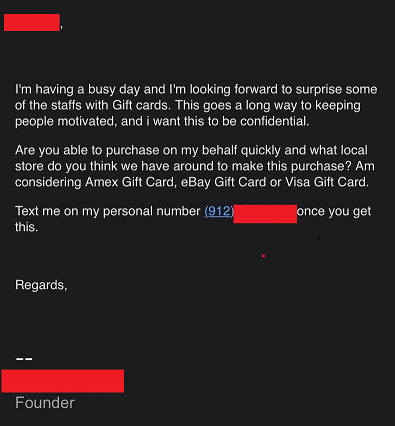
The image above shows a phishing email that attempts to get an employee to send the founder of the company gift cards. The phisher uses authority, notice the last line of the email it says “founder”. Usually, employees must drop whatever task they are working on and start working on whatever the boss wants. This phishing email takes advantage of the founder’s authority. The phisher says “I want this to be confidential” which once again comes from the boss, an employee most likely will follow what is written in the email. At a young age, kids are taught the importance of listening to authority figures. The phisher exploits this to try to get the employee to buy the gift cards. What employee would not want free gift cards?
One way to determine if your boss sent the email would be to use the company’s phone directory to confirm that the phone number is right. If you already have your boss’s phone number, give your boss a quick call asking if they sent the email. If they have no idea what you are talking about, then it is likely a scam email. Even if the email says not to bother your boss, you should at least try to call them or talk to their assistant to confirm that the boss sent the email.
To recap, the fact the supposed “boss” sent the email randomly asking you to buy gift cards should raise some red flags. Also, the fact that they want you to keep the buying of the gift cards confidential is also a red flag. Phishers and scammers will often say this so a third party does not talk them out of buying the cards.
Imitation
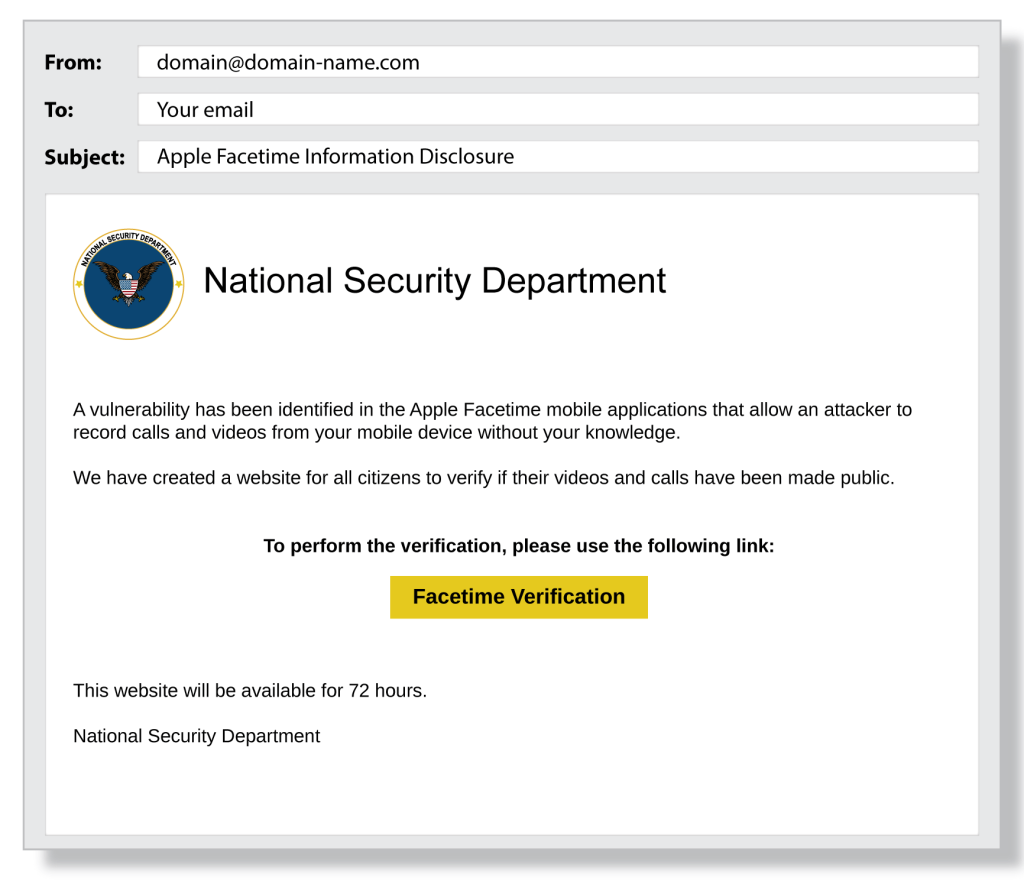
In this phishing email, the phisher uses the threat of a vulnerability and the fact that the supposed email comes from the National Security Department to attempt to scare the user into clicking the yellow button. The phisher also uses the urgency that the site will only be active for seventy-two hours.
Scarcity
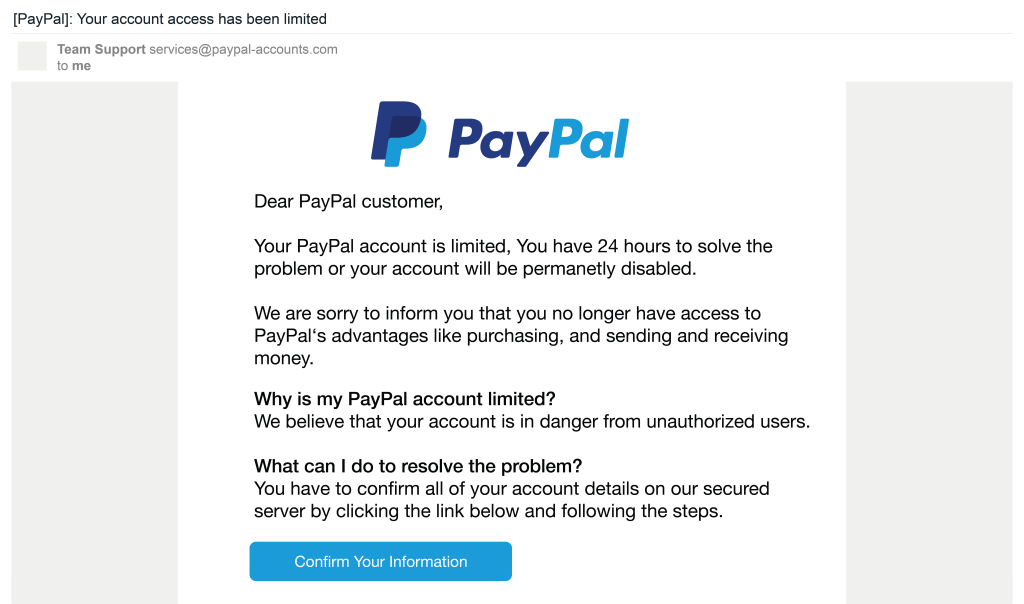
The phisher used scarcity by stating that the user’s account is limited. The blue button on the bottom probably links to a PayPal phishing page where when the user enters their password it will send the password to the threat actor. The phisher also used urgency as a tactic to put pressure on the user to click the button at the bottom of the email. The email account shows that it’s “PayPal-account.com” instead of paypal.com, which is a big red flag.
Familiarity
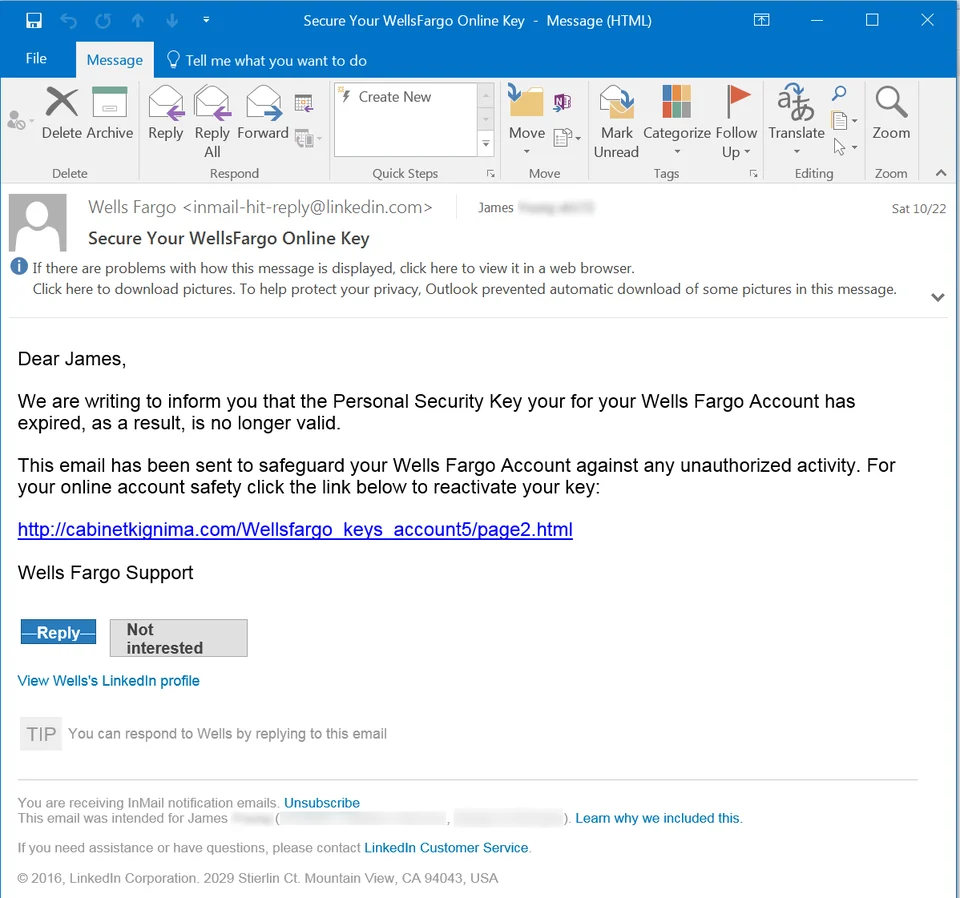
The phisher in the email used the first name of the email user, this is to build familiarity. By using the name of the email user, the phisher is making the user feel like the email was written just for them. It is similar to when the bellhop uses the name of the guest when delivering food or items. Also, they choose the name “Well Fargo”, the name of a known popular bank to build trust. The phisher is hoping that you have an account with them which will make the email feel real.
Trust

One common method a threat actor will use is to start an email chain with the victim by having a regular conversation with them. They might email back and forth for a couple of months to build a rapport with the victim, by building up trust. Another topic threat actor will compromise an email address, find old emails sent by the owner of the email account, and respond to emails with malicious documents or phishing pages. The threat actor will abuse the trust that was already built to trick the user into entering their password or downloading a malicious file thinking that the real owner of the email address sent the file or link.
Urgency
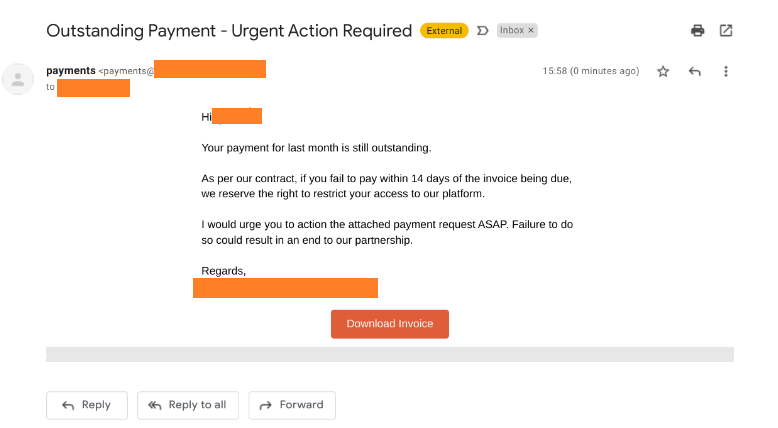
The image above shows how phishers will use urgency to try to get you to download an “invoice” which is likely a malicious document that when opened will infect your computer with malware. They also use the consequence of ending the partnership to get you to download the invoice and take action. The phisher also puts a time limit of fourteen days in an attempt for you to take action faster.
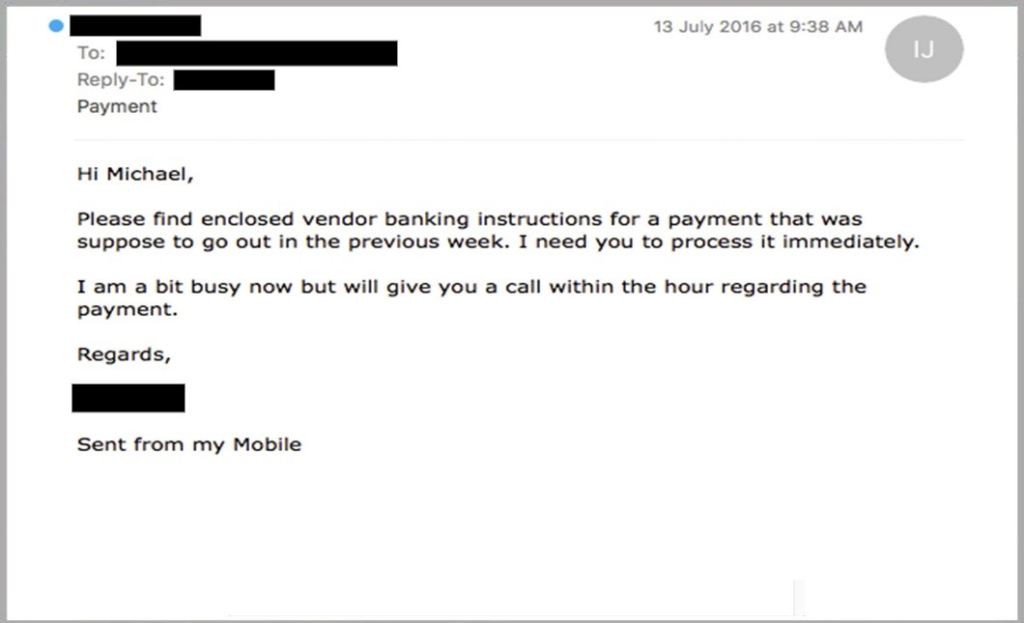
The phishing email above once again uses the urgency of a missed payment to try to attempt to get Michael to send a payment. The phisher also added the verbiage that the transfer needs to be processed immediately. If you are not expecting the payment or have no clue what it is about then it most likely is a scam.
One way to defend against this scam is to confirm with the recipient via a phone call or a different method of communication to confirm that the payment was not received or if there really needs to be a payment.
Another little trick is to look at the email address that sent the email and make sure it is not spoofed or nonofficial email. If the sender is using public emails such as google.com, hotmail.com, yahoo.com, etc. It is likely a scam. If the sender’s email address belongs to a domain, open up a new tab in the browser and type in the site in the URL bar. After visiting the site, find a way to contact the owner and ask them if they received the payment.
Consensus
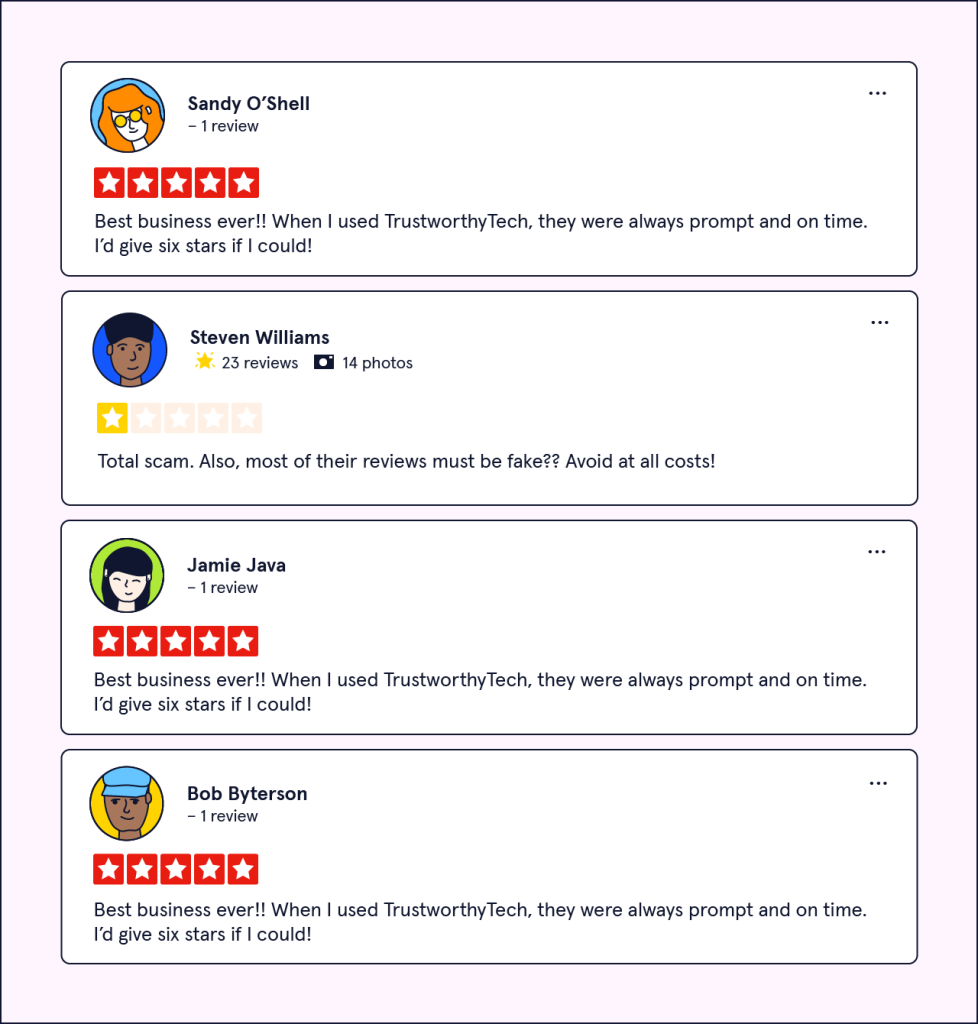
source: https://www.codecademy.com/learn/cyber-attacks/modules/social-engineering/cheatsheet
Hackers might comment on forums or review sites with comments that make the site look legit with good reviews. For example, recently I bought a sweatshirt from this online store Before buying the sweatshirt I googled the site to check its reviews. The reviews were great, all 5 stars. I ended up buying the sweatshirt. Sadly I was scammed, the sweatshirt never came and the site ended up stealing my debit card information. Shortly after I got a call from my bank saying someone in the Philippines tried to use my card. Luckily my bank stopped the charge and gave me a new debit card.
The image above shows how hackers can make fake reviews for a phishing site and bury the reviews that are negative. Signs that the reviews might be fake is that the author only has one review. Use the same or similar verbiage or where posted in a short amount of time.
Conclusion

If you fall victim to one of these phishing scams, do not worry. It can happen to even the most experienced people, especially if you are in a hurry. The first thing I would do if I were in the situation is run an anti-virus scan on my computer. Next, change the password to your email if you think you entered your password into a phisher page. Next report and mark the email as phishing. Also, I would change other account information that might be compromised.

